TermWeb OpenId Connect authentication supports only Authorization Code Flow with Authentication Method Basic and POST.
Example of configuration:
oidc.enabled=true oidc.origin=<origin URL> oidc.client.id=<client id> oidc.client.secret=<client secret> oidc.client.secret.basic=true (true to use Basic authentication, otherwise POST will be used) oidc.basic.auth.preemptive=true (true when send Basic authentication header with first request) oidc.auth.url=<authentication endpoint> (adds to <origin URL>) oidc.token.url=<token endpoint> (adds to <origin URL>) oidc.userdetails.url=<user details endpoint> (adds to <origin URL>) oidc.scopes.requested=openid profile email oidc.userdetails.field.client=termweb_client_name (field to identify client can be skipped when default client is configured) oidc.userdetails.field.default.client=admin (when client name can't be retrieved from user details) oidc.userdetails.field.user=preferred_username (field to identify user, stored as username in TermWeb) oidc.autocreate.users=true (aut create user when it not exists) oidc.login.as.guest.when.usermissing=false
In order to test authentication a user using OpenId Connect, you need to access the following URL:
<TermWeb URL>/login-oidc?origin=<origin URL>
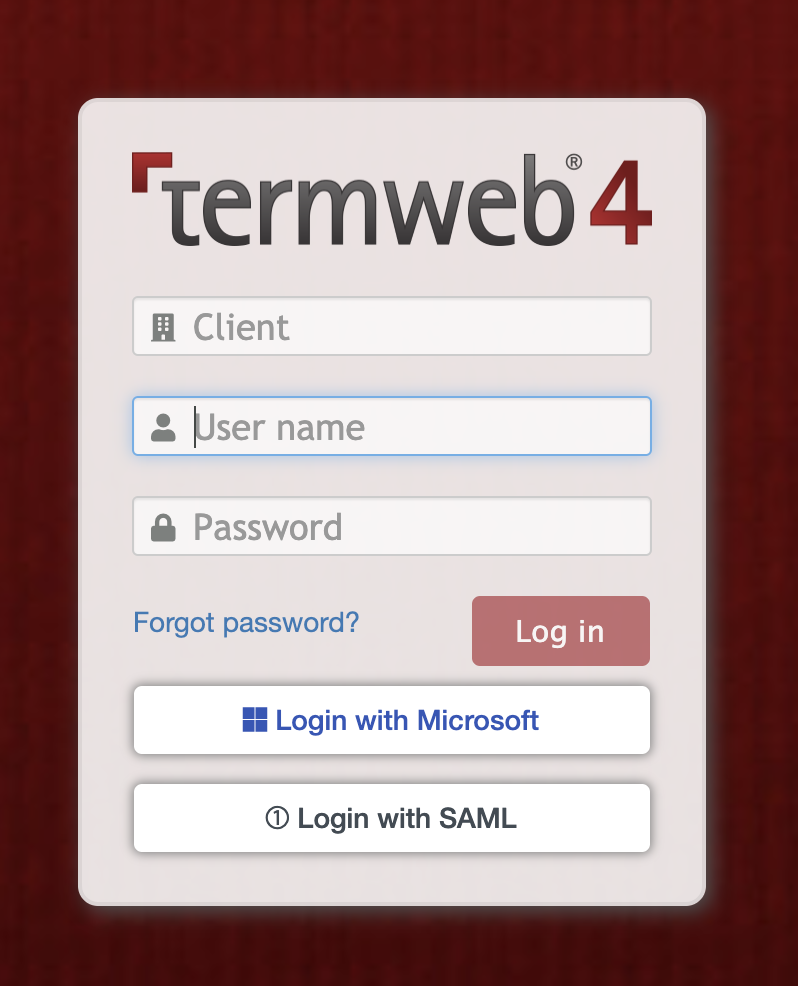
Enabling external login buttons
After release 4.0.5-9
To configure buttons for external logins, like SAML or OIDC, you need to find string "@externalLoginURLs@" and replace with values like this:
[
{
label: 'Login with Microsoft',
url: '/login-oidc?origin=https://login.microsoftonline.com/<tenant-id>',
autologin: false,
icon: 'fab fa-microsoft',
styleStr: 'color:#2f55b9; font-weight:500;'
},
{
label: '① Login with SAML',
url: '/login-saml/ssologin',
styleStr: 'color:#414b54; font-weight:500;'
}
]